
| Course Index |
|---|
| Part 1 – Introduction: What is IPv6 |
| Part 2 – IPv6 Addressing & Subnetting |
| Part 3 – IPv6 Headers & Header Extensions |
| Part 4 – ICMPv6 & IPv6 Neighborships |
| Part 5 – IPv6 Configuration, EUI-64, SLAAC & Dual Stack |
| Part 6 – IPv6 DHCP (DHCPv6) |
| Part 7 – IPv6 on Windows |
| Part 8 – IPv6 on Linux |
| Part 9 – IPv6 on Mac |
| Part 10 – IPv6 DNS, Monitoring & Address Management |
| Part 11 – IPv6 Routing |
| Part 12 – IPv6 Security & Tunneling |
| Part 13 – IPv6 Internet Connection & Address Planning |
IPv6 Security
This section covers all the critical things you need to know about IPv6 security. Some things are common sense, some are identical to measures for IPv4 and some are new. Read through the following chapters carefully and make sure you follow all best practices. Or watch my short explanation video right here:
IPv4 Security Best Practices you need to follow
- Always disable all network services that are not needed.
- Always disable all network interfaces that are not needed.
- Only use switches with hardware forwarding, as software forwarding can failin case of a DDOS.
- Limit all network management access to your network infrastructure (use Access Lists etc.)
- Always Limit management protocols like SNMP as much as possible to only the needed destinations.
IPv6 Security Best Practices you need to follow
The first rules are shared between IPv4 and IPv6, so they might ring a bell. Always make sure to implement current software versions, check for bug fixes and keep configuration on a level you fully understand and can maintain and troubleshoot. Additionally:
- Always disable all network services that are not needed.
- Always disable all network interfaces that are not needed.
- Only use switches with hardware forwarding, as software forwarding can fail in case of a DDOS.
- Limit all network management access to your network infrastructure (use Access Lists etc.)
- Always Limit management protocols like SNMP as much as possible to only the needed destinations.
- Disable router advertisements on links that are not directly connected to clients.
IPsec and its Integration into IPv6
The Internet Protocol Security suite, in short IPsec handles encryption for IPv6.
It is available for IPv4 and IPv6.
With IPv4, the implementation of IPsec was optional but with IPv6 it is now mandatory and the necessary fields are reserved in the header.
Other than before, IPsec VPN is now possible on all IPv6-capable devices!
IPsec also handles authentication of routing protocols as you have learned before.
This Wikipedia article on IPsec is well-written and goes in depth.
All the Recommended IPv6 Security Features you should implement to stay safe!
- Firewalls in general work like with IPv4 and have to be planned and engineered with just the same care!
- The following ICMP message types should always be permitted
as of RFC4890 (Recommendations for Filtering ICMPv6 Messages in Firewalls):
- Destination Unreachable (Type 1)
- Packet Too Big (Type 2) -> needed for Path MTU Discovery (PMTUD)
- Time Exceeded (Type 3, Code 0) -> needed for traceroute
- Parameter Problem (Type 4, Code 1+2) -> Destination Options, Extension Headers
- Echo Request (Type 128) -> Ping
- Echo Response (Type 129) -> Ping Reply
| Recommended IPv6 Security Features for Campus Networks | ||
|---|---|---|
| Core | 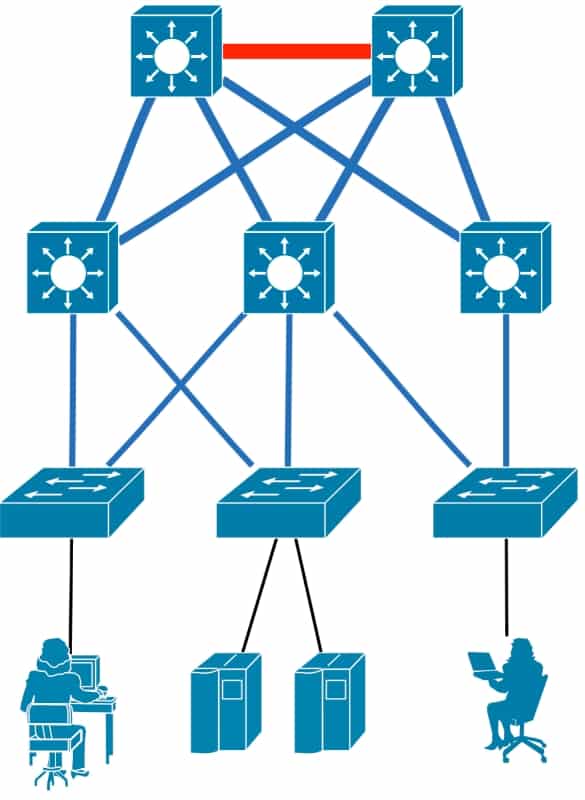 | Routing Authentication |
| Distribution | Routing Authentication Unicast RPF (Reverse Path Forwarding) Default Gateway Authentication IPv6 ND Binding Limit IPv6 Device Tracking | |
| Access | IPv6 Snooping IPv6 ND Inspection IPv6 ND Binding Limit IPv6 Device Tracking IPv6 RA Guard DHCPv6 Guard IPv6 SEND + CGA IPv6 Port-Based ACLs Traffic Storm Control Port Security Private VLANs |
Security Attacks against IPv6 you need to know about
In order to secure your network, you need to know what common IPv6 attacks can be used against IPv6 and how to mitigate them.
Let’s jump right in:
IPv6 Neighbor Discovery ND cache exhaustion Attack
Attack vector #1:
A host sends traffic to many different target addresses in the same network or prefix (e.g. with an nmap port scan) and causes a neighbor cache overflow!
IPv6 Security fix:
The IPv6 Neighbor Discovery ND resolution cache should be limited, similar to rate limiting
Attack vector #2:
A malicious host announces a lot of IPv6 addresses via Neighbor Advertisement (NA). This can cause a neighbor cache overflow.
IPv6 Security fix:
Most current operating systems ignore unsolicited Neighbor Advertisement (NA) messages already.
IPv6 Malicious Router Advertisements Attack
Attack vector:
A malicious host sends Router Advertisements (RA) and announces itself as the (preferred) router. This can lead to a man in the middle attack, if all traffic is sent via the malicious host and can be altered or recorded by the attacker.
IPv6 Security fix:
Enable Router Advertisement Guard “RA Guard” (RFC6105) on the access switch toward clients. Switch ports become role based by RA Guard, so the switch drops Router Advertisements on non-marked non-router ports.
IPv6 DHCPv6 spoofing Attack
Attack vector:
A malicious host distributes DHCPv6 addresses to clients. This can harm network security and can create a man in the middle attack, if wrong information is presented to real clients.
IPv6 Security fix:
Enable DNS Shield (RFC7610) or “DHCPv6 Guard” (Cisco proprietary) on the access switch facing all clients. The switch ports become role based and the switch will drop all DHCPv6 advertisements on non-marked non-server ports.
IPv6 source address spoofing (backscatter) Attack
Attack vector:
A malicious host sends packets with a spoofed (incorrect) source address. This can cause reply packets to be sent to this fake source address, which might be the address of a real host. This is sometimes called backscatter attack, because the victim’s host can receive overwhelming traffic from those un solicited replies.
IPv6 Security fix:
Enable Reverse Path Forwarding (RPF) on your Layer 3 switches and routers. This will discard packets that are coming in on an interface where the source address is not reachable from.
IPv6 Routing Protocol Attacks
Attack vector:
A malicious host injects wrong routing information into the routing domain. This can cause all kinds of problems, from man in the middle attacks to just broken networking overall, with poor chances to troubleshoot and find.
IPv6 Security fix:
- Secure the routing protocols OSPFv3, PIM (Multicast Routing Protocol) and RIPng using IPsec (with IPv6 Extension Headers).
- Secure the routing protocols EIGRP, BGP, IS-IS, HSRP and VRRP using MD5 authentication.
IPv6 Unwanted Tunneling Attacks
Attack vector:
A malicious host builds an unwanted tunnel into the Internet and opens the network to the outside, bypassing all IPv6 firewalls. This can also mean other hosts from the outside are able to gain full access to the internal network, bypassing all firewalls.
IPv6 Security fix:
- Filter IP protocol 41 on your firewalls. This disables all tunneling for 6in4, 6to4, 6rd and ISATAP tunnels. In my opinion, this kind of tunneling is not needed anymore, definitely not in an enterprise or production environment.
- Filter access to the official 6to4 relay address: 192.88.99.1 on your firewalls.
- Filter the Teredo protocol using UDP/3544 and Tunnel Setup Protocol using UDP/3653 on your firewalls.
IPv6 Tunneling
Watch my IPv6 tunneling video or read the written version below the video.
Tunneling IPv6 Gateway to Gateway
Tunneling was a major feature in the early days of IPv6 because the Internet was not end-to-end IPv6 capable, since most providers implemented IPv6 late.
To connect the many IPv6 islands, it was necessary to implement some tunnels over IPv4.
Today this is neither necessary nor recommended, because native IPv6 connectivity is working well and should be preferred. If there is no native IPv6 connectivity, then native IPv4 connectivity should strongly be preferred over tunneling.
The following part is shortened because I find IPv6 tunneling deprecated but want you to still know what kinds were available:
- static IPv6-in-IPv4 (6in4) tunnel
- static GRE tunnel
- 6to4
- IPv6 Rapid Deployment (6rd)
- DS-Lite
- LISP
IPv6-in-IPv4 (6in4) Tunneling
- IPv6-in-IPv4, commonly called 6in4 is a static tunnel.
- Both tunnel ends have IPv4 addresses configured.
- IPv6 addresses are statically configured on the tunnel.
- IPv6 packets are encapsulated in IPv4 before being sent via the IPv4-only infrastructure.
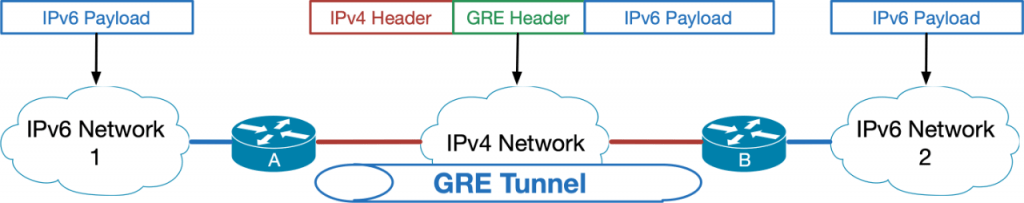
GRE Tunnel for IPv6 (Generic Routing Encapsulation) explained
A GRE Tunnel (Generic Routing Encapsulation) is a common way to tunnel all kinds of traffic. It is still used today.
- GRE is a static tunnel.
- Both Tunnel ends have IPv4 addresses configured.
- IPv6 addresses are configured on top of the tunnel
- IPv6 packets are encapsulated in GRE packets (protocol 47) before being sent over the IPv4-only transit path
6to4 IPv6 Tunneling
6to4 is an automatic tunnel. It can offer access to the public IPv6 Internet via IPv4-only infrastructure.
- Public 6to4 relay servers are available
- There are major risks, such as no support for and no control over the public tunnel endpoints. This can lead to serious IPv6 security issues (man in the middle, traffic logging, …)
- The operator of a public relay is unknown.
- Performance is not known and not guaranteed.
- Suboptimal routing is possible and even probable
Summary: don’t do it. Read RFC3964 Security Considerations for 6to4 for more information.
6rd – IPv6 Rapid Deployment Tunneling
6rd – IPv6 Rapid Deployment is another migration strategy for fast IPv6 deployments over IPv4 only backend or transit infrastructure.
The 6rd mechanism was defined in RFC5569 and is based on 6to4 methods.
It enables Internet Service Providers or ISPs to deploy IPv6 quickly to customers, without the need for full end-to-end IPv6 support in Access and Aggregation Layers.
The 6rd prefix is addressed from the provider’s own IPv6 prefix.
Tunneling IPv6 Host to Gateway
The following Host to Gateway Tunneling methods enable IPv4-only clients to automatically establish connectivity to an IPv6 gateway server and enable IPv6 connectivity over this tunnel.
These methods were available:
- Teredo
- ISATAP
- Tunnel Broker
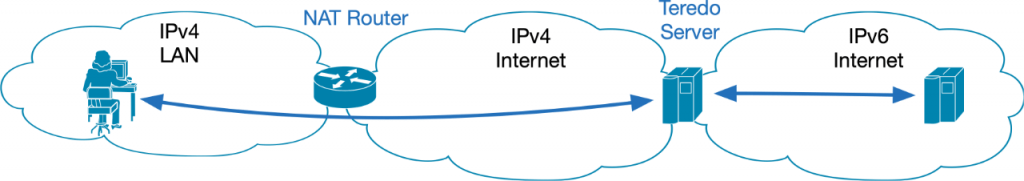
Teredo IPv6 Tunneling for Clients
Teredo was developed by Microsoft and defined in RFC4380.
- It was implemented since Windows XP and Windows Server 2008.
- Teredo clients are addressed from static prefix 2001::/32.
- IPv6 packets are encapsulated in UDP to enable support for NAT that might be in place between client and gateway server. NAT was common in IPv4 deployments especially in residential access scenarios such as DSL.
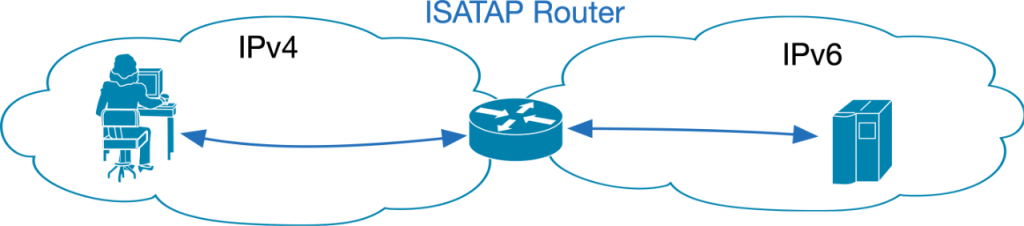
ISATAP (Intra-Site Automatic Tunnel Addressing Protocol) for Clients
ISATAP or in long form the Intra-Site Automatic Tunnel Addressing Protocol enables host to router communication and was defined in RFC5214.
- IPv6 packets are encapsulated in IPv4 packets to be sent over IPv4-only infrastructure.
- There is no support for IPv6 multicast.
Steps for ISATAP:
- The ISATAP client generates a Link-Local IPv6 address from its IPv4 address.
- The ISATAP clients sends a Router Solicitation (RS) message to the upstream ISATAP router. The ISATAP server address is either statically configured or received by DNS lookup of isatap.${domain}.
- The ISATAP server sends a Router Advertisement message (RA) to the learned IPv4 address of the client.
- The ISATAP client generates an IPv6 address from the Router Advertisement message.
- IPv6 traffic is always sent via the ISATAP router (including traffic to other ISATAP clients) -> This can lead to a serious bottleneck and poor performance.
Tunnel Broker & SixXS IPv6 Tunneling for Testing
Mostly for power users at home, or to try out IPv6, there were two Tunnel Broker options available in the past:
- tunnelbroker.net by Internet service provider Hurricane Electric (HE) and
- SixXS
Both sites had different tunneling mechanisms available. SixXS has since been shut down as of 2017-06-06.
The Tunnel from client to tunnel broker server is established over the existing IPv4 network. Installation was fairly simple and the service was (and is in the case of tunnelbroker.net) good enough to test drive IPv6 from home, if you have no native connectivity from your ISP yet.
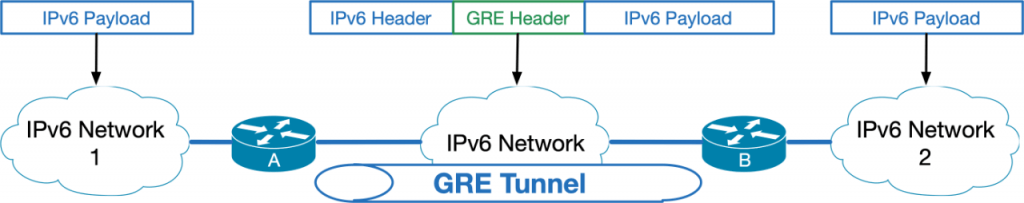
Tunneling IPv6 over IPv6 – Just use GRE
To tunnel IPv6 traffic over IPv6 infrastructure, the most common and best practice approach is to use a static GRE (Generic Routing Encapsulation) tunnel.
- Both tunnel ends are configured with IPv6 addresses.
- IPv6 addresses are configured on top of the tunnel.
- You can secure the tunnel optionally with IPsec.
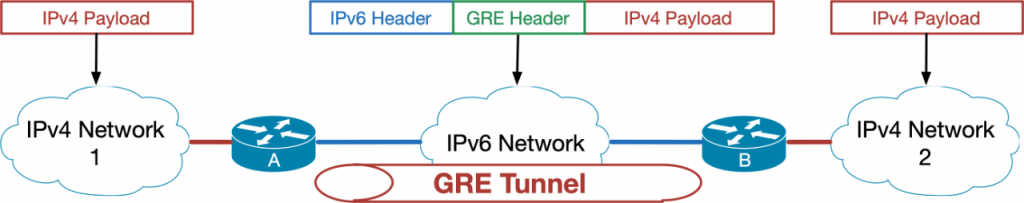
Tunneling IPv4 over IPv6 – GRE is best
The last tunneling option is maybe for future use. Imaging an IPv6 Internet, which still has some old IPv4 islands, which are not connected to each other anymore. Poor them!
They should be connected via IPv4 over IPv6 using a static Generic Routing Encapsulation (GRE) tunnel:
- The tunnel ends are configured with IPv6 addresses.
- IPv4 addresses are configured on top of the tunnel.
- You can secure the tunnel optionally with IPsec.
Recommended Resources for additional reading
Apart from the links throughout this course I recommend the following resources for additional information:
- The Internet Society (ISOC) IPv6 Portal
- Test your IPv6 connectivity on test-ipv6.com
- The official IANA list of assigned IPv6 address space is very interesting
- The Google IPv6 deployment statistics
- The RIPE NCC IPv6 working group and mailing list
Book recommendations on IPv6
I can recommend the following 3 books which I enjoyed reading:



This concludes IPv6 Foundation Part 12: IPv6 Security & Tunneling of the original IPv6 Foundation Master Class.
Previous Part: IPv6 Foundation Part 11: IPv6 Routing
Next Part: IPv6 Foundation Part 13: IPv6 Internet Connection Planning

